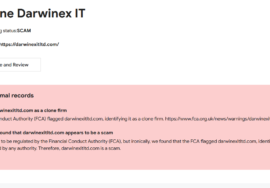
Inside the World of Crypto Reclaim — KeystonePrimeLtd.com Reveals the Hidden Layers of Bitcoin Recovery
Inside the World of Crypto Reclaim — KeystonePrimeLtd.com Reveals the Hidden Layers of Bitcoin Recovery
In the evolving world of cryptocurrency, one thing remains certain: no digital crime is ever truly invisible. Behind every stolen Bitcoin and every fraudulent trading site, a permanent trace lives on the blockchain. Few understand this truth better than the team at KeystonePrimeLtd.com, who have built a reputation for uncovering the hidden layers of crypto recovery using a blend of forensic science, data intelligence, and international collaboration.
1. Enter the Digital Forensics Lab
At the heart of KeystonePrimeLtd.com’s recovery work lies a state-of-the-art forensic operations center where blockchain data isn’t just read, it’s decoded.
Here, analysts don’t see Bitcoin as random transactions. They see digital fingerprints. Every address, hash, and timestamp contributes to a broader map of movement. These clues reveal how stolen Bitcoin travels across exchanges, mixers, and even privacy coins.
Example:
Olivia, a software developer, lost 2 BTC through a fake investment app that disappeared overnight. Within two weeks, KeystonePrimeLtd.com’s forensic lab reconstructed the entire money trail identifying three intermediary wallets and one final exchange endpoint under regulatory watch.
2. Blockchain Analytics Where Science Meets Persistence
Blockchain analytics is a fusion of data science and detective work. Using advanced visualization tools, KeystonePrimeLtd.com maps the transaction flow of stolen funds, even when scammers attempt to “chain-hop” between cryptocurrencies.
Their analysts use heuristic clustering, machine learning, and transaction graphing to connect wallets that appear unrelated but aren’t. These insights are then used to flag suspect exchanges or recoverable endpoints.
Technical Insight:
Each Bitcoin transfer leaves a permanent ledger entry. KeystonePrimeLtd.com’s analysts convert this raw blockchain data into dynamic visual models, allowing them to see how thousands of addresses link together in seconds.
3. The Human Element — Global Intelligence Networks
Crypto recovery doesn’t happen in isolation. KeystonePrimeLtd.com’s success is built on strong relationships with:
- Exchange compliance departments (Binance, Coinbase, and others)
- Law enforcement agencies specializing in cybercrime
- Regional blockchain intelligence units across Europe, Asia, and North America
This global tracing network allows faster coordination when freezing illicit accounts or submitting legal evidence. It’s how they bridge the gap between forensic discovery and actionable recovery.
Real-World Example:
A cross-border case involving stolen Bitcoin from a U.S. trader was resolved when KeystonePrimeLtd.com’s analysts alerted an Asian crypto exchange, leading to an immediate asset freeze before the thief could cash out.
4. Tools of the Trade — Beyond the Blockchain Explorer
Most victims know of blockchain explorers like Etherscan or Blockchain.com, but professional recovery teams use far more sophisticated software suites.
KeystonePrimeLtd.com leverages enterprise-grade platforms capable of:
- Identifying exchange wallets through metadata tagging
- Tracking token swaps across multiple chains
- Linking IP data from past wallet interactions
These tools, combined with proprietary in-house technology, turn what seems like digital chaos into traceable order.
5. Verification — Turning Forensic Data into Legal Evidence
For recovery to hold up in court, evidence must be verifiable. KeystonePrimeLtd.com’s analysts meticulously document every transaction, timestamp, and wallet address involved in the investigation.
Each report includes blockchain screenshots, technical annotations, and statistical validation of trace confidence. This chain-of-custody documentation gives law enforcement and courts the legitimacy needed to act.
6. The Role of Artificial Intelligence in Modern Recovery
AI is redefining crypto recovery. KeystonePrimeLtd.com uses machine learning algorithms to identify suspicious wallet patterns, predict scam behavior, and flag new money-laundering tactics before they mature.
By automating the identification of recurring wallet clusters, their system can instantly detect if a stolen fund’s trail intersects with previous scam networks.
Insider Note:
In 2025 alone, AI-assisted tracing helped KeystonePrimeLtd.com link more than 40 fraudulent operations to just 12 master wallets, a breakthrough that led to multiple law enforcement actions.
7. Education and Empowerment for Victims
Beyond their investigations, KeystonePrimeLtd.com also educates victims and investors on how recovery really works. They demystify blockchain tracing, explain legal options, and guide users on protecting themselves from future attacks.
Their goal is simple: to replace panic with proof, and confusion with clarity.
The Hidden Power of Transparency
Bitcoin’s greatest weakness, its anonymity is also its greatest strength. Every transaction is permanent, every path traceable, and every theft leaves a mark that technology and teamwork can uncover.
KeystonePrimeLtd.com has turned this principle into a recovery revolution, empowering victims to reclaim what was stolen and teaching the world that transparency, not secrecy, defines the true future of crypto.
If your Bitcoin was stolen through a fake platform or online scam, remember this: somewhere in the blockchain, your proof still exists and with expert help, recovery is not a dream but a data-driven possibility.